March 28, 2018
Why Secure, POS Merchant Services Improve the Patient Billing Experience

High-profile data breaches are constantly in news headlines. These security concerns are leaking into the healthcare world, with a rise in data breaches over the last several years. Ponemon’s Annual Benchmark Study on Privacy and Security of Healthcare Data found that almost 90 percent of healthcare providers experienced at least one breach in the last 24 months. Another 40 percent of those had more than five breaches.
What Data Is at Risk?
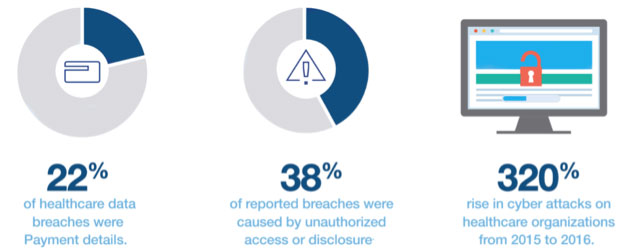
Perpetrators will attempt to steal all data types including medical records, payment details, and insurance information. Common targets areas are medical files, billing & insurance records, payment details, monthly statements, scheduling details, and prescription records. Hackers generally profit from their attempts by selling the data for cash, or holding data hostage for ransom.
How Are Payment Systems Susceptible?
In a healthcare system, the weak points of payment security include point-of-sale (POS) systems, websites, and malware. POS software is typically targeted in a data breach, as it can allow the installation of malware. Healthcare providers are moving toward online payment and mobile device transactions as well – security in these access points is also critical.
How to Reduce Risk
The first step in creating a solution is to understand the problem. Cyber attacks on healthcare organization are on the rise, increasing 320 percent from 2015 to 2016 according to a 2017 Redspin report. To address the elevated threat, healthcare organization need solutions that:
- Increase payment card security
- Remain compliant with PCI requirements
- Reduce the scope of the card data environment
- Segment residual card data onto a network separate from clinical and EHR data
Payment Card Industry Data Security Standards Compliance (PCI-DSS) is the generally recognized set of security standards that organizations must adhere to if they accept credit card payments. The basic policies include controlling card data access, monitoring and tracking card data, and addressing information security within the organization with third party vendors. Compliance with PCI-DSS requires ongoing attention and vigilance.
Security Layers to Implement
To ensure security, a layered approach is recommended – above and beyond the PCI-DSS standards. Additional tools are available to reduce fraud and discourage hacking These include:
- EMVⓇ(Europay, Mastercard, and Visa) are the chip-enabled cards that have become the new standard. It’s estimated that in 2017, 98% of cards issues in the U.S. will be chip cards. EMV cards offer a higher level of security than traditional magnetic strip because the the chip enables card authentication to verify that the card is legitimate. Business receiving transactions have moved toward updating their card readers to work with chip cards, and healthcare organizations are also adopting these practices.
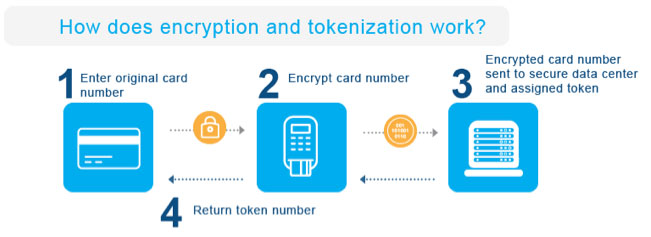
- Encryption is used to scramble the card data into a different form – cipher text – while it travels through the POS system and over the payment network. The cipher text cannot be easily read except with the authorized “decoder”.
- Tokenization removes the card data from the provider’s environment which protects the card data at rest. The card number is replaced by a randomly generated token, which makes it useless to thieves, but allows it to remain “on file” in a safe way. The token is specific to the merchant or business, so it doesn’t carry any information if intercepted by an outside source.
A comprehensive approach to data security, including and especially in the payment process, is critical to keeping patient data secure during their healthcare interactions. For more information and access to the tools and solutions to increase security, request a demo or connect with us on Twitter, LinkedIn, or Facebook to learn more.